Robust File and Folders copy (Robocopy)
By default Robocopy will only copy a file if the source and destination have different time stamps or different file sizes.
Robocopy
Some of the useful swtiches:
robocopy \\server01\folder01 \\server02\folder02 /e /copyall
Copy everything under folder01 to folder02 (includes all files attributes, security settings, time stamp), empty folders included.
robocopy \\server01\folder01 \\server02\folder02 /s /copyall
Copy everything under folder01 to folder02 (includes all files attributes, security settings, time stamp), empty folders not included.
robocopy \\server01\folder01 \\server02\folder02 /e /copyall /create
Create folders and files structure for everything under folder01 at folder02 (includes all files attributes, security settings, time stamp), empty folders included. Good for testing folders migration.
robocopy \\server01\folder01 \\server02\folder02 /e /copyall /move
Move everything under folder01 to folder02 (includes all files attributes, security settings, time stamp), empty folders included.
Search This Blog
Thursday, April 22, 2010
Login script : Map network drive VBS script
Using VBS script to map network drive allows you to map different users from different groups to different paths using a single script.
Pros:
1. Less maintenance required, in case of modification, only 1 script needs to be modified.
2. Centralized control. 1 single GPO.
Cons:
1. Extra scripting needs to be done for special users.
2. Not as granular as having different login script for different groups.
WshNetwork.MapNetworkDrive
Creating Login Scripts
Here is an example of my modified script.
=====================================
' Default drive letter for User and Department Shared Folder
Const User_drive = "H:"
Const Dept_drive = "G:"
' Define User Location
' E.g. For user in TPM, they should be group under "DLMYO-TPM All Staff"
Const TPM = "CN=DLMYO-TPM All Staff"
' Define Security Groups property here.
' E.g. for IA, Group name is "DLMYO-IA-SERVER".
Const BCP = "cn=DLMYO-BCP"
Const TSS = "cn=DLMYO-TSS"
Const IA = "cn=DLMYO-IA-SERVER"
Const EMC = "cn=DLMYO-EMC"
Const DCM = "cn=DLMYO-DCM"
Dim wshDrives, i
Set wshNetwork = CreateObject("WScript.Network")
Set ADSysInfo = CreateObject("ADSystemInfo")
Set CurrentUser = GetObject("LDAP://" & ADSysInfo.UserName)
strGroups = LCase(Join(CurrentUser.MemberOf))
' Loop through the network drive connections and disconnect any that match User_drive and Dept_Drive
Set wshDrives = wshNetwork.EnumNetworkDrives
If wshDrives.Count > 0 Then
For i = 0 To wshDrives.Count-1 Step 1
If wshDrives.Item(i) = User_Drive Then
wshNetwork.RemoveNetworkDrive User_drive, True, True
Elseif wshDrives.Item(i) = Dept_drive Then
wshNetwork.RemoveNetworkDrive Dept_drive, True, True
End If
Next
End If
' Map User folder depending on user's location
If InStr(1, strGroups, TPM, 1) Then
wshNetwork.MapNetworkDrive User_drive, "\\aosrv008\Users\" & wshNetwork.UserName, TRUE
End If
' Map department shared folder depending on user's security group
If InStr(1, strGroups, BCP, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\BCP"
ElseIf InStr(1, strGroups, TSS, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\TSS"
ElseIf InStr(1, strGroups, IA, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\IA"
ElseIf InStr(1, strGroups, EMC, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\EMC"
ElseIf InStr(1, strGroups, DCM, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\DCM"
End If
wscript.echo "Departmental shared folder G: and User personal folder H: were mapped."
=====================================
Pros:
1. Less maintenance required, in case of modification, only 1 script needs to be modified.
2. Centralized control. 1 single GPO.
Cons:
1. Extra scripting needs to be done for special users.
2. Not as granular as having different login script for different groups.
WshNetwork.MapNetworkDrive
Creating Login Scripts
Here is an example of my modified script.
=====================================
' Default drive letter for User and Department Shared Folder
Const User_drive = "H:"
Const Dept_drive = "G:"
' Define User Location
' E.g. For user in TPM, they should be group under "DLMYO-TPM All Staff"
Const TPM = "CN=DLMYO-TPM All Staff"
' Define Security Groups property here.
' E.g. for IA, Group name is "DLMYO-IA-SERVER".
Const BCP = "cn=DLMYO-BCP"
Const TSS = "cn=DLMYO-TSS"
Const IA = "cn=DLMYO-IA-SERVER"
Const EMC = "cn=DLMYO-EMC"
Const DCM = "cn=DLMYO-DCM"
Dim wshDrives, i
Set wshNetwork = CreateObject("WScript.Network")
Set ADSysInfo = CreateObject("ADSystemInfo")
Set CurrentUser = GetObject("LDAP://" & ADSysInfo.UserName)
strGroups = LCase(Join(CurrentUser.MemberOf))
' Loop through the network drive connections and disconnect any that match User_drive and Dept_Drive
Set wshDrives = wshNetwork.EnumNetworkDrives
If wshDrives.Count > 0 Then
For i = 0 To wshDrives.Count-1 Step 1
If wshDrives.Item(i) = User_Drive Then
wshNetwork.RemoveNetworkDrive User_drive, True, True
Elseif wshDrives.Item(i) = Dept_drive Then
wshNetwork.RemoveNetworkDrive Dept_drive, True, True
End If
Next
End If
' Map User folder depending on user's location
If InStr(1, strGroups, TPM, 1) Then
wshNetwork.MapNetworkDrive User_drive, "\\aosrv008\Users\" & wshNetwork.UserName, TRUE
End If
' Map department shared folder depending on user's security group
If InStr(1, strGroups, BCP, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\BCP"
ElseIf InStr(1, strGroups, TSS, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\TSS"
ElseIf InStr(1, strGroups, IA, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\IA"
ElseIf InStr(1, strGroups, EMC, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\EMC"
ElseIf InStr(1, strGroups, DCM, 1) Then
wshNetwork.MapNetworkDrive Dept_drive, "\\aosrv008\DCM"
End If
wscript.echo "Departmental shared folder G: and User personal folder H: were mapped."
=====================================
Permission control for NTFS folders
Understanding the permission setting in the ACL is crucial for administrating file servers especially for controlled shared folders.
Understanding Windows Server 2008 File and Folder Ownership and Permissions
The ACL GUI is separated into basic permission (the top half of the GUI) and special permission (advanced mode). Basic permissions are actually built up from special permissions, giving a convenient way for users to assign permission without having to go thru the full list of special permissions.
===========================================
Basic Permissions for folders
Full Control : Permission to read, write, change and delete files and sub-folders.
Modify : Permission to read and write to files in the folder, and to delete current folder.
List Folder Contents : Permission to obtain listing of files and folders and to execute files.
Read and Execute : Permission to list files and folders and to execute files.
Read : Permission to list files and folders.
Write : Permission to create new files and folders within selected folder.
The following table outlines the basic file permissions:
Full Control : Permission to read, write, change and delete the file.
Modify : Permission to read and write to and delete the file.
Read and Execute : Permission to view file contents and execute file.
Read : Permission to view the files contents.
Write : Permission to write to the file.
===========================================
Special Permissions
Traverse folder / execute file : Allows access to folder regardless of whether access is provided to data in folder. Allows execution of a file.
List folder / read data : Traverse folder option provides permission to view file and folder names. Read data allows contents of files to be viewed.
Read attributes : Allows read-only access to the basic attributes of a file or folder.
Read extended attributes : Allows read-only access to extended attributes of a file.
Create files / write data : Create files option allows the creation or placement (via move or copy) of files in a folder. Write data allows data in a file to be overwritten (does not permit appending of data).
Create folders / append data : Create folders option allows creation of sub-folders in current folder. Append data allows data to be appended to an existing file (file may not be overwritten)
Write attributes : Allows the basic attributes of a file or folder to be changed.
Write extended attributes : Allows extended attributes of of a file to be changed.
Delete subfolders and files : Provides permission to delete any files or sub-folders contained in a folder.
Delete : Allows a file or folder to be deleted. When deleting a folder, the user or group must have permission to delete any sub-folders or files contained therein.
Read permissions : Provides read access to both basic and special permissions of files and folders.
Change permissions : Allows basic and special permissions of a file or folder to be changed.
Take ownership : Allows user to take ownership of a file or folder.
===========================================

Before starting to modify the permission, you might want to stop inheriting ACL from the parent folders. Under advanced > change permission, uncheck "Include inheritable permissions from this object's parent"
So in general,

For read only users, you will assign - List folders content, Read and Execute, Read.

For read and write users - List folders content, Read and Execute, Read, Write.

For administrators - Full control.
You can also use command line to modify the permission.
ICACLS - command line to configure ACL
Understanding Windows Server 2008 File and Folder Ownership and Permissions
The ACL GUI is separated into basic permission (the top half of the GUI) and special permission (advanced mode). Basic permissions are actually built up from special permissions, giving a convenient way for users to assign permission without having to go thru the full list of special permissions.
===========================================
Basic Permissions for folders
Full Control : Permission to read, write, change and delete files and sub-folders.
Modify : Permission to read and write to files in the folder, and to delete current folder.
List Folder Contents : Permission to obtain listing of files and folders and to execute files.
Read and Execute : Permission to list files and folders and to execute files.
Read : Permission to list files and folders.
Write : Permission to create new files and folders within selected folder.
The following table outlines the basic file permissions:
Full Control : Permission to read, write, change and delete the file.
Modify : Permission to read and write to and delete the file.
Read and Execute : Permission to view file contents and execute file.
Read : Permission to view the files contents.
Write : Permission to write to the file.
===========================================
Special Permissions
Traverse folder / execute file : Allows access to folder regardless of whether access is provided to data in folder. Allows execution of a file.
List folder / read data : Traverse folder option provides permission to view file and folder names. Read data allows contents of files to be viewed.
Read attributes : Allows read-only access to the basic attributes of a file or folder.
Read extended attributes : Allows read-only access to extended attributes of a file.
Create files / write data : Create files option allows the creation or placement (via move or copy) of files in a folder. Write data allows data in a file to be overwritten (does not permit appending of data).
Create folders / append data : Create folders option allows creation of sub-folders in current folder. Append data allows data to be appended to an existing file (file may not be overwritten)
Write attributes : Allows the basic attributes of a file or folder to be changed.
Write extended attributes : Allows extended attributes of of a file to be changed.
Delete subfolders and files : Provides permission to delete any files or sub-folders contained in a folder.
Delete : Allows a file or folder to be deleted. When deleting a folder, the user or group must have permission to delete any sub-folders or files contained therein.
Read permissions : Provides read access to both basic and special permissions of files and folders.
Change permissions : Allows basic and special permissions of a file or folder to be changed.
Take ownership : Allows user to take ownership of a file or folder.
===========================================

Before starting to modify the permission, you might want to stop inheriting ACL from the parent folders. Under advanced > change permission, uncheck "Include inheritable permissions from this object's parent"
So in general,

For read only users, you will assign - List folders content, Read and Execute, Read.

For read and write users - List folders content, Read and Execute, Read, Write.

For administrators - Full control.
You can also use command line to modify the permission.
ICACLS - command line to configure ACL
File Server Resource Manager (FSRM) : Auto Quotas

FSRM define quota based on folders (not by users). Hence there's a function to auto populate quota definition for any sub-folders created.
Configuring Volume and Folder Quotas
With this, you just need to define auto quota for the parent folder, and all sub-folders will be applied with the quota. Including newly created sub-folders.
List ACLs for folders and all sub-folders
CACLS or ICACLS provides you with the list of ACL for a targetted folder.
E.g.
C:\>icacls "c:\New folder"
c:\New folder NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(M)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
MYORIGIN\a182456:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
Successfully processed 1 files; Failed processing 0 files
When combined with VBS, we can recursively call for sub-folders to generate ACL for full list of folders.
Quick and easy ACL printout
E.g.
C:\>icacls "c:\New folder"
c:\New folder NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(M)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
MYORIGIN\a182456:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
Successfully processed 1 files; Failed processing 0 files
When combined with VBS, we can recursively call for sub-folders to generate ACL for full list of folders.
Quick and easy ACL printout
Thursday, April 15, 2010
ICACLS : command line to configure ACL for files and folders.

ICACLS can be used to configure the ACL of files and folders via command line.
The GUI interface is easier to configure for a few folders, but if you are dealing with hundreds of folders. It will be take a long time to finish.
"ICACLS /?" for a full list of parameters.
I have used ICACLS to do the following:
1. Stop inheriting permissions, and keep the current inherited permission.
>ICACLS
2. Remove "Authenticated Users" from the ACL
>ICACLS
3. Grant Read, Write and Execute rights for UserA
>ICACLS
VPN L2TP over IPsec
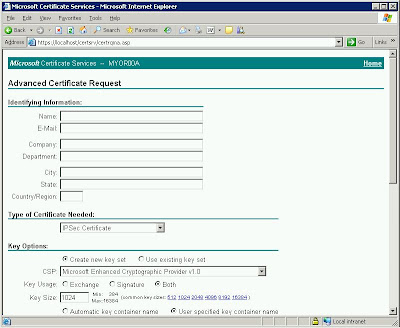
Network team is proposing a cheaper VPN solution compared with current check point secure clients. We will be using Juniper VPN router, which is using L2TP connection on top of IPsec encryption.
1. Configure a CA server in Directory Service.
2. Use the CA server to manage the certificates for clients and Juniper router.
The CA server was installed on a 2003 domain controller.
1. Go to add\remove programs. add windows component. check certificate services and click OK.
2. Specify whether it's a enterprise CA or stand alone CA (Stand alone recommended for IPsec cert purpose)
3. decide the Distinguished Name for the CA, the life span of the cert and where to store the logs.
3. Get ready 2003 CD as certsrv.ex_ and certsrv.dll are required.
For IPsec cert request.
1. If you are using Stand Alone CA, nothing need to be configured on the Certificate Authority.
2. If you are using Enterprise CA, you will need to configure the certificate templates to issue IPsec and IPsec (Offline Request).
a. Go to the CA server. Administrator tools > Certificate Authority.
b. Expand the CA server. Navigate to Certificate Templates and right click > new..
c. Select the IPsec and IPsec (Offline Request) template to be issued.
If you are using Windows 2003 CA and you have Windows 7 and Vista users in the environment.
1. A patch is required for the page to be displayed properly. The patch is to be installed on the CA server.
How to use Certificate Services Web enrollment pages together with Windows Vista or Windows Server 2008
You might also need to establish the CA server IIS service to publish the website via SSL.
1. Go to IIS service on the CA server.
2. Right click on Default web site > properties.
3. Go to Directory Security and select Server certificate.
4. Go thru the wizard and request for a cert from the CA server you have previously installed.
Configure SSL on you website with IIS
Once you have done the setup for CA service. You can proceed with managing the certificate for Juniper router and user PCs.
Configuring a Dial-up VPN Using Windows XP Client with L2TP over IPsec.pdf
Tuesday, April 6, 2010
User access denied to folder even though effective permission is Full Control
Having problem with a folder where a user is joined to a group, full control permission is assigned to this group. Yet when accessing this folder, we hit access denied problem.
I check the security permission via the following steps:
1. Logon to the server using Domain\Administrator account. (the builtin domain admin account)
2. Go to D:
3. Right Click empty space on the D: window and choose properties.
4. Select the security tab.
5. Here are the permissions that I see:
a. Creator Owner : Special
b. Domain Admins : Full Control
c. System : Full Control
d. Administrators (Local) : Full Control
6. As you can see Domain Admins has Full Control access to this volume/folder.
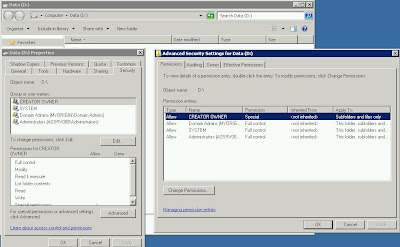
I then logon to the server using my account "lim, alex" (my account is a member of Domain Admins) and attempt to go to D:
1. Logon to server using Domain\alex account.
2. Go to D: (At Start > Run > type D: and enter)
3. Hit access denied message.
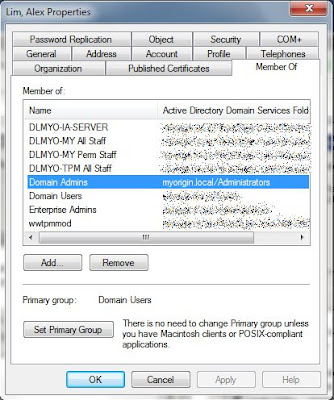
I then check on the effective permission using Administrator account
1. Logon to server using Domain\Administrator.
2. Go to security of D:
3. Go to Advanced > Effective Permission tab.
4. Select user "lim, Alex" and saw all permission allowed.
Related Discussion:
User access to files and folders
I check the security permission via the following steps:
1. Logon to the server using Domain\Administrator account. (the builtin domain admin account)
2. Go to D:
3. Right Click empty space on the D: window and choose properties.
4. Select the security tab.
5. Here are the permissions that I see:
a. Creator Owner : Special
b. Domain Admins : Full Control
c. System : Full Control
d. Administrators (Local) : Full Control
6. As you can see Domain Admins has Full Control access to this volume/folder.

I then logon to the server using my account "lim, alex" (my account is a member of Domain Admins) and attempt to go to D:
1. Logon to server using Domain\alex account.
2. Go to D: (At Start > Run > type D: and enter)
3. Hit access denied message.

I then check on the effective permission using Administrator account
1. Logon to server using Domain\Administrator.
2. Go to security of D:
3. Go to Advanced > Effective Permission tab.
4. Select user "lim, Alex" and saw all permission allowed.

Related Discussion:
User access to files and folders
Windows 7 : Remote Server Administration Tools
To install the Various Admin Tools just like 2000/2003 Admin Packs, Windows 7 has its own pack call the RSAT (Remote Server Administration Tools)
The below gives you the instruction to download and install the pack on Windows 7
Remote Server Administration Tools for Windows 7


The below gives you the instruction to download and install the pack on Windows 7
Remote Server Administration Tools for Windows 7


Monday, April 5, 2010
Windows XP : Unable to find Security Tab.
Open Windows Explorer, go to Tools, Folder Options, View and uncheck Use Simple File Sharing.
Windows XP : Security enhancement for Internet kiosk

The followings are the settings down on the EMC Internet Kiosk PC.
1. GPEDIT.MSC
2. User Configuration > Administrative Templates > Start Menu and Taskbar
a. Remove Programs on Settings Menu.
b. Remove Network Connections from Start Menu.
c. Remove Search menu from Start Menu.
d. Remove Run menu from Start Menu.
e. Remove My Pictures icon from Start Menu.
f. Remove My Music icon from Start Menu.
g. Remove My Network Places icon from Start Menu.
h. Remove Drag-and-drop context menus on the Start Menu.
i. Prevent changes to Taskbar and Start Menu Settings.
j. Remove access to the context menus for the taskbar.
k. Turn off user tracking.
l. Remove frequent programs list from the Start Menu.
m. Remove Set Program Access and Defaults from Start Menu.
3. User Configuration > Administrative Templates > Control Panel
a. Prohibit access to the Control Panel.
4. Remove Everyone's permission on these 2 files:
a. %SystemRoot%\Inf\Usbstor.pnf
b. %SystemRoot%\Inf\Usbstor.inf
5. Regedit, HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UsbStor, Change "Start" value to 4 Hexadecimal.
Related Links:
How can I prevent users from connecting to a USB storage device?
How to disable USB sticks and limit access to USB storage devices on Windows systems
Subscribe to:
Comments (Atom)